Don’t invest unless you’re prepared to lose all the money you invest. This is a high-risk investment and you are unlikely to be protected if something goes wrong. Take 2 minutes to learn more
Service for copy trading. Our Algo automatically opens and closes trades.
The L2T Algo provides highly profitable signals with minimal risk.
24/7 cryptocurrency trading. While you sleep, we trade.
10 minute setup with substantial advantages. The manual is provided with the purchase.
79% Success rate. Our outcomes will excite you.
Up to 70 trades per month. There are more than 5 pairs available.
Monthly subscriptions begin at £58.
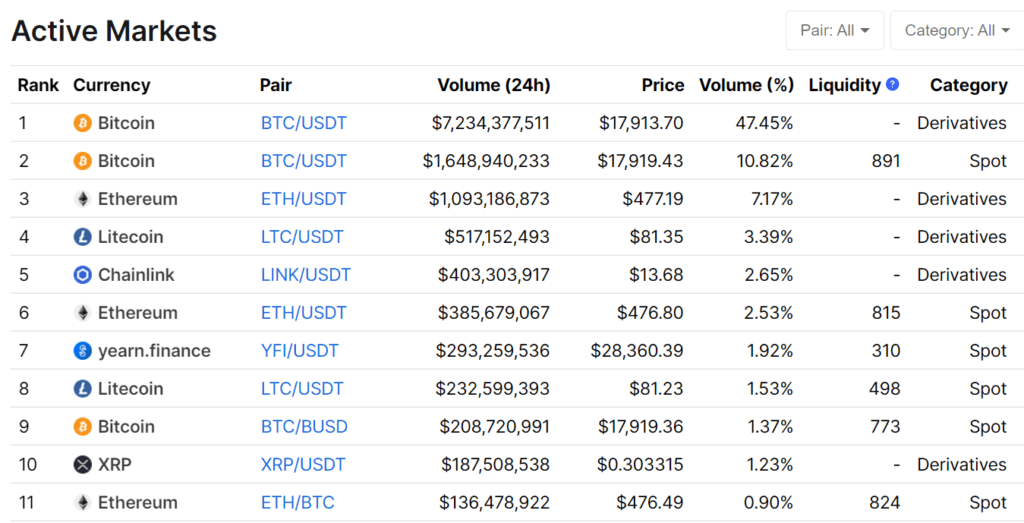
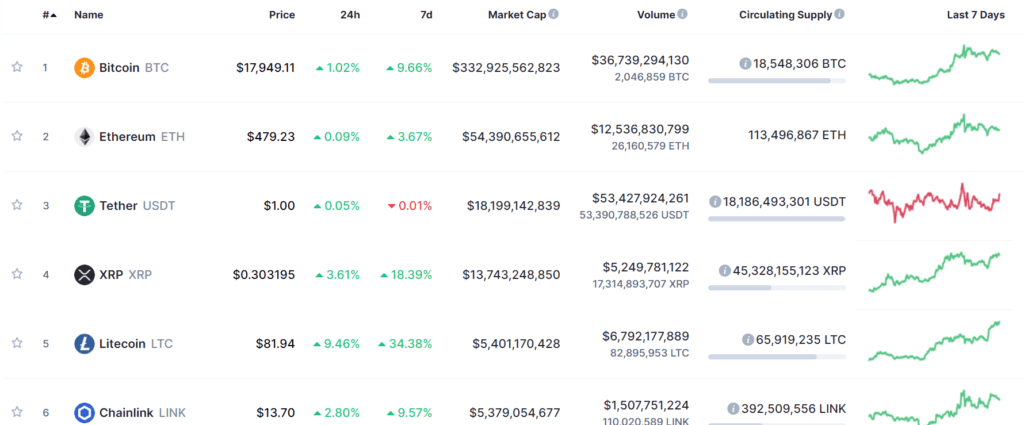
The cryptocurrency trading scene is now a multi-billion dollar battleground. Not only does this include popular digital currencies like Bitcoin, Ethereum, and Ripple – but heaps of less liquid cryptocurrencies, too.
However – and much like any online trading arena, buying and selling cryptocurrencies with the view of making money is not easy. On the contrary, you need to have a super in-depth understanding of technical analysis.
The good news is that there is an alternative to needing to spend months and months learning how to read digital currency charts – Telegram crypto signals. Put simply, by joining a top-rated signal service like Learn 2 Trade – you will receive cryptocurrency trading suggestions directly via the Telegram app.
Fancy finding out more about how Telegram crypto signals can allow you to stay ahead of the curve in this innovative trading sphere? If so – this guide will explain everything you need to know about the Learn 2 Trade Telegram cryptocurrency signal service!
Table of Contents
Learn 2 Trade Free Signals Service
- Get 3 Free Signals per Week
- No Payment or Card Details Needed
- Test the Effectiveness of our High-Level Signals
- Major, Minor, and Exotic Pairs Covered
What are Telegram Crypto Signals?
Before we get to the nitty-gritty, we first need to explain what cryptocurrency signals actually are. In its most basic form, signals are trading suggestions that are sent to you in real-time.
This might come via SMS message, email, or an instant messaging app like Telegram. The signal itself will contain a series of instructions that allow you to profit from an expert trader’s research.
- For example, the signal might tell you to buy BTC/USD at $14,500 because the RSI indicator is signaling that the pair is oversold.
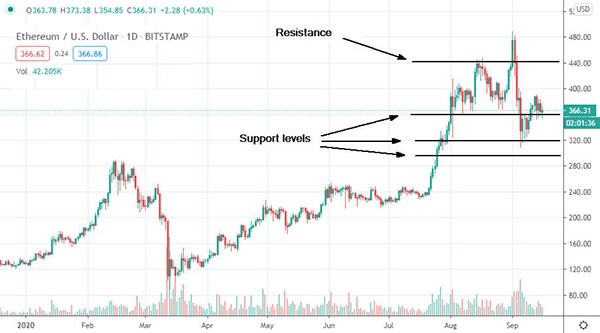
- Similarly, a signal might tell you to short-sell ETH/EUR because a key support line has just been broken.
In addition to the pair and entry price, the best Telegram cryptocurrency signals will tell you what stop-loss and take-profit orders to set up. Put simply, this ensures that you can trade cryptocurrencies while at the same time mitigating your risks.
Who are Telegram Crypto Signals Suitable for?
Telegram crypto signals are suitable for a variety of financial goals and experience profiles. In other words, whether you are a complete cryptocurrency trading newbie or an experienced investor with little time on your hands – signals could be the solution that you are looking for.
Here’s why:
You Have no Idea how to Trade Crypto
It goes without saying that Telegram crypto signals are highly conducive for actively trading, without having any experience. This is because you do not need to perform any research or analysis. On the contrary, the Telegram cryptocurrency signal service will give you all of the entry and exit prices that you need to place at your chosen broker.

8cap - Buy and Invest in Assets

- Minimum deposit of just 250 USD to get lifetime access to all the VIP channels
- Buy over 2,400 stocks at 0% commission
- Trade thousands of CFDs
- Deposit funds with a debit/credit card, Paypal, or bank transfer
- Perfect for newbie traders and heavily regulated

You Don’t Have Time to Actively Research Crypto Trends
Leading on from the section above, Telegram crypto signals are also ideal for those that lack the time to actively trade. Sure, you will still need to place the respective buy and sell orders that the signals instruct you to act on. But, you will be able to cut out hours of daily research that is otherwise required to succeed in the crypto trading scene.
This is because the research and analysis process is taken care of by your chosen Telegram crypto signal provider. For example, we at Learn 2 Trade have a team of experienced in-house traders that perform in-depth technical analysis throughout the week. As soon as we find a trading opportunity, a team member will update our signal members via the Telegram app.
You Want to Diversify Into Several Trading Markets
Let’s suppose that you are an expert trader with a great track record in making consistent gains. If this is the case, then you will know firsthand that there are only so many financial assets that you can focus on.
For example, you might know the ins and outs of a select number of cryptocurrency pairs – but you couldn’t possibly become an expert in all of them.
Instead, your chosen signal provider will have the skills, experience, and technological assistance to scan heaps of assets and financial instruments.
For example, not only does Learn 2 Trade have experienced in-house traders that are specialists in cryptocurrencies – but other assets, too. This includes forex, stocks, indices, and even commodities like gold and oil.
You want Access to a Cryptocurrency Trading Community
The benefits of being part of a fully-fledged crypto trading community should not be understated. This is because you will have access to like-minded people that all wish to achieve the same goal – to make money from the multi-billion dollar cryptocurrency markets.
When using a Telegram crypto signal service like Learn 2 Trade, you will have access to almost 5,000 members. While some will be inexperienced (maybe like yourself), others will have years of experience in the space. This does, of course, also include our team of in-house traders too.
How do Telegram Crypto Signals Work?
So now that we have explained who Telegram crypto signals might be suitable for, we now need to dive a little bit deeper into how this area of the trading scene actually works.
After all, you are going to be risking your own trading capital when acting on a signal, so it’s important for you to understand how things actually work before taking the plunge.
All Trading Order Details Provided
When you receive a signal from Learn 2 Trade, you will receive everything you need to act on it. That is to say, we don’t stop at just proving you with the cryptocurrency pair and entry price. On the contrary, you will be provided with the required target exit price and stop-loss level.
Here’s an example of what a Learn 2 Trade Telegram crypto signal would look like:
- Pair: XRP/USD.
- Order: Sell.
- Limit Order: $0.2890.
- Take-Profit: $0.2689.
- Stop-Loss: $0.2970.
- Recommended Risk: 1%.
As you can see from the above, there are six pieces of data that you will always receive from our Telegram crypto signals. At the forefront of this is the cryptocurrency pair that you should trade and whether you should opt for a buy or sell order.
And of course – this also includes the required entry price. In this case, that’s a buy limit order on XRP/USD at $0.2890. What you might find with a lot of crypto signal providers in the space is that this is all you will receive. In other words, while you have the trading suggestion and recommended entry price – you need to come up with your own exit strategy.
This goes against the nature of what a Telegram crypto signal service should look like, which is why we always supply a stop-loss and take-profit price with all of our suggestions.
- As you can see from the example above, we suggest a stop-loss price of $0.2970.
- If the trade subsequently went against us and XRP/USD hit $0.2970 – the position would automatically be closed.
This ensures that we keep our risk levels to a minimum.
- Additionally, we opted for a take-profit price of $0.2689.
- Much like the aforementioned stop-loss order, if this price is reached in the market then our trade will be closed automatically.
Only this time, at our target profit price. As we uncover in more detail shortly, our Telegram crypto signals always carry a risk and reward ratio. For example, we might risk 1% to make a 4% profit, or risk 2% to make a 5% profit. Either way, this will be reflected in the stop-loss and take-profit levels that come with the respective Telegram crypto signal.
How we Outperform the Cryptocurrency Market
You might be wondering how we actually derive our Telegram crypto signals. After all, it is all good and well sending out trading suggestions – anyone can do that. But, we at Learn 2 Trade have historically defended a 76% win ratio – meaning that over the course of time we yield more winning trades than losing ones.
Put simply, our Telegram crypto signals are generated on the back of in-depth research by our team of in-house traders. The vast bulk of this is dominated by technical analysis, albeit, our team also keeps tabs on the fundamentals.
Additionally, it’s not just about finding trends. This is because our team of traders also works hard to find the best entry and exit prices. Ultimately, this ensures that we limit our losses in the event a crypto signal doesn’t go to plan. This is imperative, as not all of our signals will return a profit. Any provider that tells you differently is simply not being honest.
Why is Telegram Used for Crypto Signals?
Trading signals have been around for decades – long before the age of online brokerage platforms. Back then, signals were provided in the form of a telephone call. As you can imagine, this was nothing short of cumbersome and costly. Then signal providers made the transition to email once online trading became a thing.
While this is still used by a lot of crypto signal platforms today, it is still somewhat inefficient. After all, there is every chance that you do not see the email in time to act on the signal and thus – miss the opportunity. This is why the Learn 2 Trade crypto service utilizes Telegram.
As soon as one of our in-house traders sends out a signal, it will send a notification to your Telegram app. As long as you have sound notifications turned on, you will never miss a signal. In addition to this, Telegram allows us to get more interactive with our signals.
For example, we’ll often send out images of our technical analysis findings so that our members can view our thought-process. And of course – as we mentioned earlier, Telegram is superb for creating a trading community. All you need to do is join our group and you will have the opportunity to discuss market insights with almost 20,000 fellows Learn 2 Trade members.
Risk Management
Make no mistake about it – all forms of trading come with an element of risk. Whether you are buying traditional equities, purchasing bonds, or trading forex pairs – there is every chance that you will lose money. This is no different from buying and selling cryptocurrencies – as an incorrect market move will result in a loss.
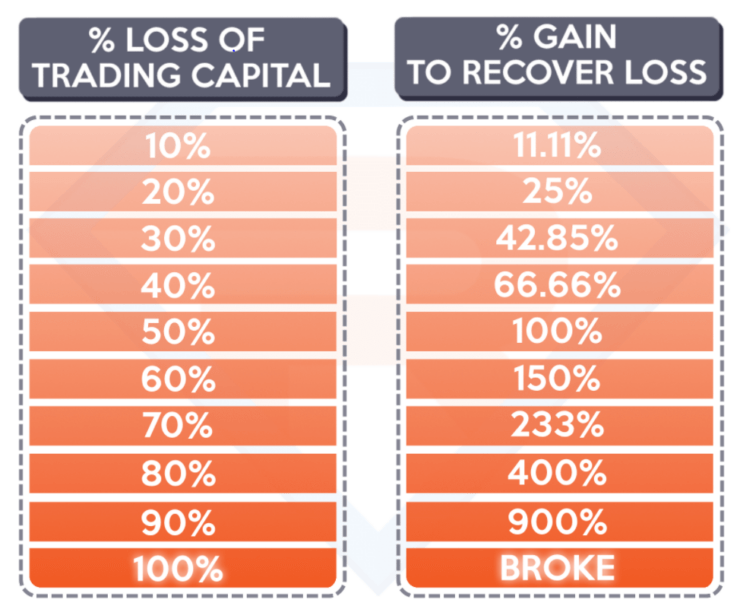
Below we cover the fundamentals of how you can use Telegram crypto signals in a risk-averse manner.
Bankroll Management
Bankroll management is a theory utilized in all trading sectors. It simply refers to the process of protecting your trading capital from large losses. The most effective and widely used way of doing this is to limit the amount you stake on a position. This is best achieved in percentage terms – against that of your current account balance.
- For example, let’s suppose that you decide to cap your stakes to 1.5%.
- If your trading capital currently stands at $4,000 – this means that you cannot risk more than $60 on a single trade.
But of course – the value of your trading balance will go up and down on each and every position that you close.
- For example, by the end of month 1, you might have increased your trading capital to $5,000.
- As such, your maximum stake now stands at $75.
- This is because your 1.5% limit is now based on $5,000, as opposed to the $4,000 that you started with.
In taking such an approach, it is highly unlikely that you will burn your trading capital. Even if you are going through a bad run of results, your maximum trade size will decline as your balance drops.
- For example, let’s say that you have a terrible second month of trading.
- In turn, your trading account balance now stands at just $3,200.
- This means that you are $800 down from your initial balance of $4,000.
- But, based on a 1.5% maximum stake, the most that you will risk on a $3,200 balance is $48.
- As you can see, this is far less than the $75 stake that you were able to risk in the prior month when your balance stood at $5,000.
Ultimately, by utilizing a risk management strategy in conjunction with our Telegram crypto signals, you can ensure that you remain in the game in the long run. At the other end of the spectrum, failure to do this can and will result in large financial losses.
Risk vs Reward Ratio
As we briefly noted earlier, all of our Telegram crypto signals come with a risk and reward ratio. Once again, this is the maximum amount that we are prepared to risk on a specific trading signal, alongside the gains that we are looking to target.
Here’s an example of how a 1:3 risk/reward ratio looks like:
- Our trading signal suggests placing a buy order on BTC/ETH at 38.50.
- 1% of our suggested entry price is 0.38. As such, our stop-loss order is set at 38.12.
- 3% of our suggested entry price is 1.15. As such, our take-profit order is set at 39.65.
As per the above, it doesn’t matter what happens with BTC/ETH price action – as only one of two things can happen. If our Telegram crypto signal is proved successful, then our order will be closed at a 3% profit when the pair hits 39.65. But, if the markets move against us, we limit our losses to 1% when the pair hits 38.12.
Leverage
Leading on from the section above, 3% profit on a trade that might remain in play for no longer than a few hours is huge. After all, you’d need to wait years and years to earn this much by depositing your money into a traditional savings account!
However, it must be noted that you might struggle to make sufficient profits each month if your trading capital is somewhat small. For example, let’s suppose that you risked $500 on one of our crypto signals that returned gains of 3%. This would result in a super-small financial return of just $15.
As such, a lot of Learn 2 Trade signal members will apply the leverage to their positions. The amount of leverage that you are able to get will depend on the broker that you sign up with and your country of residence. This is because certain restrictions are in place – especially in Europe and Australia.
Nevertheless, if your chosen crypto trading site allows you to apply leverage of, say 1:10 – this means that your profits are magnified by a factor of 10. In turn, a small profit of $15 would translate into much bigger returns of $150.
What Crypto Pairs do our Telegram Signals Cover?
Moving into 2023, there are now thousands of cryptocurrencies in existence. In terms of actual trading pairs, you can multiply this number by double figures.
This is because each digital currency can be traded against heaps of individual coins. For example, Bitcoin can be traded against Ripple, Ethereum, Bitcoin Cash, EOS, and thousands more. Cryptocurrencies can also be traded against fiat currencies like the US dollar.
Here at Learn 2 Trade, our Telegram crypto signals cover two different branches of the space – fiat-to-crypto and crypto cross-pairs.
- Fiat to Crypto: As the name suggests, fiat to crypto pairs contain one digital currency and one fiat currency. The most traded pair of this type is BTC/USD – which will see you speculate on the exchange rate between Bitcoin and the US dollar.
- Crypto Cross-Pairs: This crypto pair type will contain two competing digital currencies. For example, BTC/ETH and EOS/XRP are crypto cross-pairs.
Ultimately, our team of in-house traders has all of the required tools to scan the cryptocurrency markets around the clock. This means that they are constantly on the lookout for trading opportunities and thus – the Telegram crypto signals that you receive will be highly diverse.
Acting on our Telegram Crypto Signals
If you’ve read our guide up to this point, then you should now have a firm grasp of how Learn 2 Trade Telegram crypto signals work. You should also have the tools to effectively deploy a risk-averse strategy – including bankroll management and understanding risk-reward ratios.
As such, the next stage of the Telegram crypto signal journey is to find a suitable trading platform. After all, you will need to use an online broker if you wish to place the entry and exit orders that our signals provide.
In the sections below we explain the core factors that you need to consider in choosing a crypto trading broker. If you don’t have time to research a platform yourself, you can read our comprehensive guide on the best cryptocurrency brokers of 2023 and beyond.
Is the Crypto Trading Site Regulated?
You probably know that the cryptocurrency trading space is still finding its feet. By this, we mean that time and time again we hear the media report on large-scale cryptocurrency exchange hacks. This is why a lot of newbie traders are put off by the industry, as there is always that niggling concern that the trading platform in question will run into problems.
With this in mind, we would strongly suggest that you only use regulated cryptocurrency brokers. This should come in the form of a reputable licensing body like CySEC or the FCA. We should, however, note that in order to benefit from these regulatory bodies, you will need to trade crypto CFDs.
This simply means that you can act on our Telegram crypto signals without needing to own the underlying asset. CFDs are actually beneficial for several reasons, as they allow you to go short and even apply leverage. Additionally, most of the crypto CFD platforms that we recommend allow you to trade in a commission-free manner.
What Pairs Does the Platform Support?
As we noted earlier, our team of in-house traders will send our crypto signals on a variety of pairs. In turn, you’ll need to make sure that your chosen broker offers a good range of cryptocurrency trading markets.
Ultimately, you don’t want to be opening accounts with lots of different providers, as this can be a logistical nightmare. Instead, it’s best to stick with a single, regulated platform that offers a highly extensive number of crypto pairs.
What Commissions Does the Broker Charge?
All cryptocurrency brokers and trading platforms are in the business of generating a profit. They do this by charging trading-related fees. Some will also make money when you deposit or withdraw funds, alongside overnight financing and inactivity fees.
But, the most important fee that you need to look out for is the trading commission charged by the broker alongside the average spread. The former is often a percentage that is multiplied by your stake.
For example, Coinbase charges 1.5% per trade, which is huge. In fact, this would make our Telegram crypto signals unviable, as our profit targets would get eaten away by the commission rate. As we noted just a moment ago, this is why we typically only recommended commission-free brokers.
In addition to this, all crypto pairs will come with a spread. This is the difference between the buy and sell price that you see on-screen. The gap between the two prices is how the broker in question guarantees a profit is made irrespective of what happens in the markets.
As such, on top of commission-free brokers, we also focus on platforms that offer tight spreads. This is especially crucial when you consider the nature of our Telegram crypto signals. That is to say, we typically opt for a profit target in the region of 3%, which wouldn’t be suitable for a cryptocurrency broker that charges high fees.
Does the Broker Support Mobile Trading?
We should also note the importance of choosing a cryptocurrency broker that supports mobile trading. In an ideal world, this should come in the form of a mobile app that is compatible with your respective operating system.
Put simply, by having access to a mobile trading app you will always be able to act on our Telegram crypto signals – as soon as the notification is distributed.
After all, there might come a time when you receive a signal but you are away from your device. If this is the case, your trading app provider will allow you to place the required orders no matter where you are located!
Free Crypto Signals Telegram
If you’re in the hunt for a free crypto signals Telegram group, you might want to pause. Think about it – the signal provider will likely be scanning the currency trading markets around the clock. Not only will they be utilizing advanced chart reading tools and technical indicators, but they will also be drawing on years of experience.
Taking this into account, do you think that the crypto signal provider will do all of this without asking for any money? Probably not. In fact, what we usually find with free crypto signals Telegram groups is that they will cover up certain parts of the trading suggestion.
For example, the free crypto signals Telegram group might tell you to go long on ETH/USD and to create a stop-loss order at $750.67. However, this signal is worthless, as you don’t have access to the suggested entry price, nor the target take-profit region.
Make no mistake about it – in order to obtain these two key pieces of data – you’ll need to pay a fee!
Crypto Signals on Telegram – Plans and Pricing
If you like the sound of what the Learn 2 Trade Telegram crypto signal service offers for your long-term financial goals, we are now going to discuss that all-important metric – pricing.
Put simply, we actually offer two different plans for you to consider. Below we explain how each crypto signal plan works in more detail.
Free Crypto Signals via Telegram
We understand that there is a lot of skepticism in the crypto signal arena, which is why we offer a free plan to all. In a nutshell, this does not require any financial information from you. Instead, you simply need to open an account and join the Learn 2 Trade Telegram group.
In doing so, you will receive 3 signals per week. Although this won’t be sufficient for you to get the most out of our crypto signal service, it does at the very least allow you to test out us. You’ll get to see the types of crypto trades that we typically deploy and what risk/reward strategies are opted for.
However – and as we explain in the section below, the premium plan comes with significantly more in the way of signals throughout the day.
Premium Crypto Signals via Telegram
By signing up to our premium crypto signal service, on average you will receive 5 suggestions per day via Telegram. This means that you will receive each and every trading suggestion that our team distributes. This usually covers all time zones, so you won’t miss out no matter which part of the world you are based.
As the name implies, the premium account does come with a fee. With that said, we believe that the prices we charge – in relation to the service and historical results achieved, offer excellent value. This is especially the case when you consider the 76% win rate we have defended to date.
Please find below the various packages that we offer on our premium Telegram crypto signal service.
- £40 per month – billed monthly.
- £89 for three months (£29.67 per month) – billed quarterly.
- £129 for six months (£21.5 per month) – billed annually.
- £215 for a year (£17.92 per month) – billed yearly.
Taking the above into account, you actually have a couple of options at your disposal if you are not sure about staying with us in the long run. Firstly, all of our plans come with a 30-day money-back guarantee.
This means that you can request a full refund if you are not happy with the service you have received. Very few of our members have ever taken advantage of this, as Learn 2 Trade satisfaction rates have historically remained high.
In addition to the money-back guarantee, we should note that you are never locked into your chosen plan. For example, if you opt for the rolling monthly plan, the longest period that you are locked in for is one month.
Similarly, if you decide to take advantage of our slightly longer plans – which come with a lower monthly rate, the longest you are locked in for is either 3 or 6 months.
How to Join our Crypto Signal Telegram Group
If you’re keen to begin making money from our Telegram crypto signals, we are now going to explain what you need to do to get started right now.
Step 1: Open a Crypto Broker Account
Your first port of call is to find a crypto trading site that is conducive to our signals. This means that the broker should be regulated and offer competitive fees.
Step 2: Choose a Learn 2 Trade Signal Plan
To start receiving our Telegram crypto signals in real-time, you will first need to decide which plan you want to start with. As noted above, this is a choice between our free and premium plans.
Step 3: Download Telegram and Join
After choosing the plan that you wish to start with, it’s then just a case of joining our Telegram group. If you don’t already have the app installed on your phone, you can download it from Google Play or App Store – free of charge.
Once you have joined our group, don’t forget to ensure that your Telegram app has sound notifications switched on. In doing so, you’ll never miss a trading opportunity again!
Crypto Signals Telegram Guide: The Verdict?
We hope that by reading this guide in full you now have a full understanding of the many benefits that Telegram crypto signals offer.
Whether that’s being able to trade digital currencies in a semi-passive manner or avoiding the need to learn technical analysis – signals allow you to access the cryptocurrency trading scene with ease.
All you need to do is join the Learn 2 Trade Telegram group and a suitable broker to place our signal suggestions!
Learn 2 Trade Free Signals Service
- Get 3 Free Signals per Week
- No Payment or Card Details Needed
- Test the Effectiveness of our High-Level Signals
- Major, Minor, and Exotic Pairs Covered
FAQs
What is a crypto signal Telegram group?
Crypto signals are trading suggestions that tell you which orders to place - based on in-depth market research. By receiving these signals via Telegram, a notification will pop-up as soon as the suggestion is sent!
How much does the Learn 2 Trade crypto signal service make?
It goes without saying that profit margins will vary from month to month. With that said, historically we have defended a 76% win rate. This means that 76 trades out of every 100 are profitable.
What crypto pairs do your signals target?
We mainly focus on major cryptocurrencies that are priced against the US dollar. This is because these markets benefit from the largest levels of liquidity of trading volumes. With that said, we do from time to time find trading opportunities on less liquid cryptocurrency pairs.
How risky are your Telegram crypto signals?
Whether or not you use our Telegram crypto signal service, all trading carries an element of risk. With that said, we never risk more than 1% on a single trade, ensuring that you stand the best chance possible of protecting your bankroll in the long run.
Do you offer a free trial?
We offer new customers a 30-day money-back guarantee on all of our premium plan purchases - no questions asked. In addition to this, we also offer a free crypto signal service that comes with 3 suggestions per week.